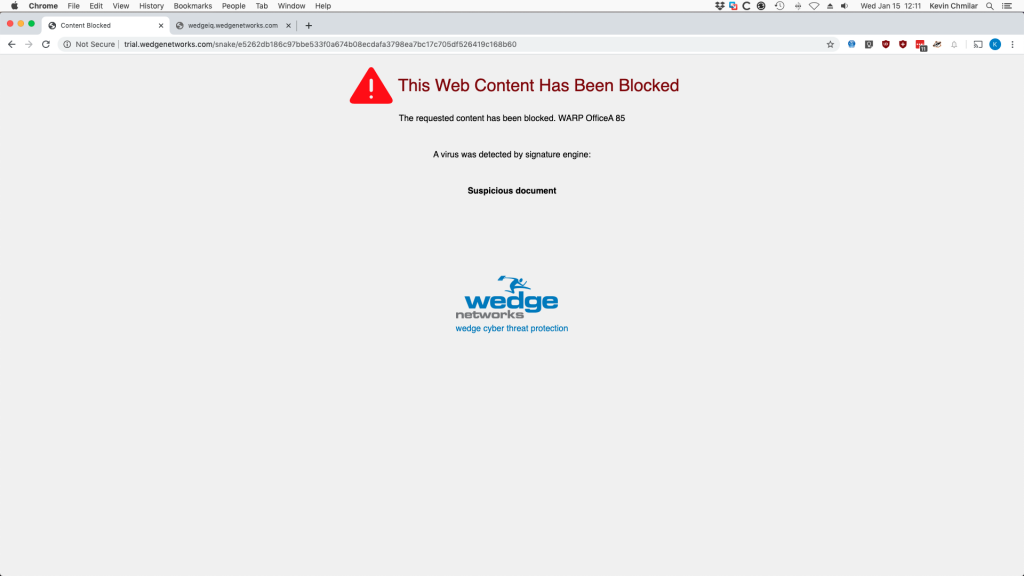
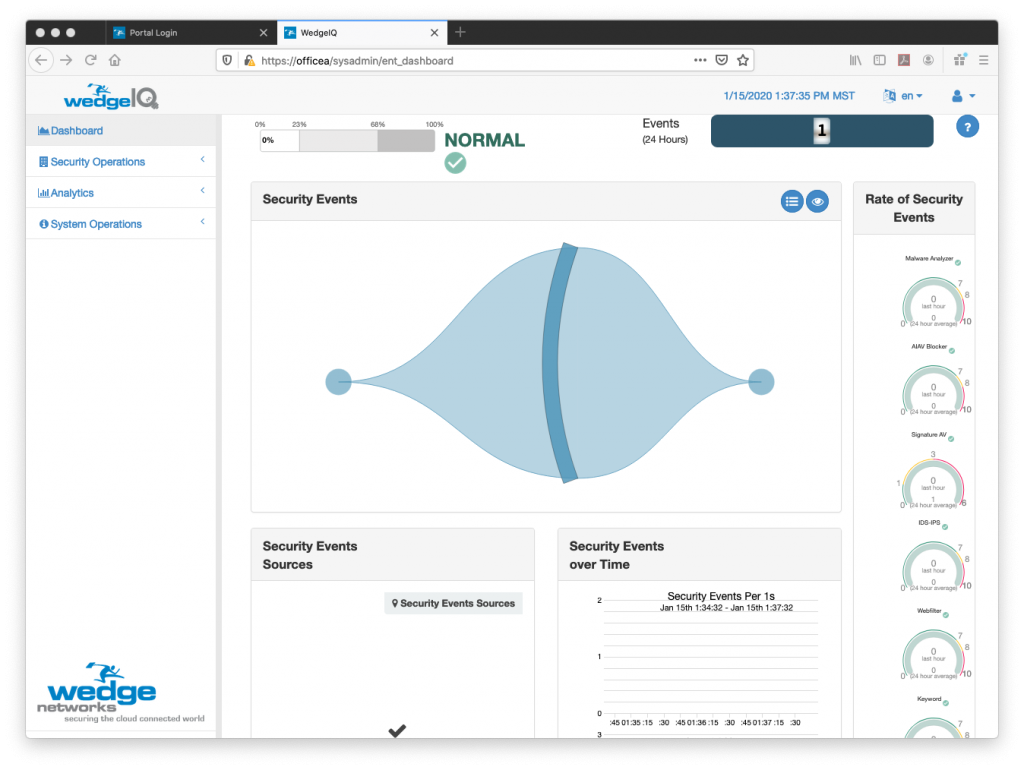
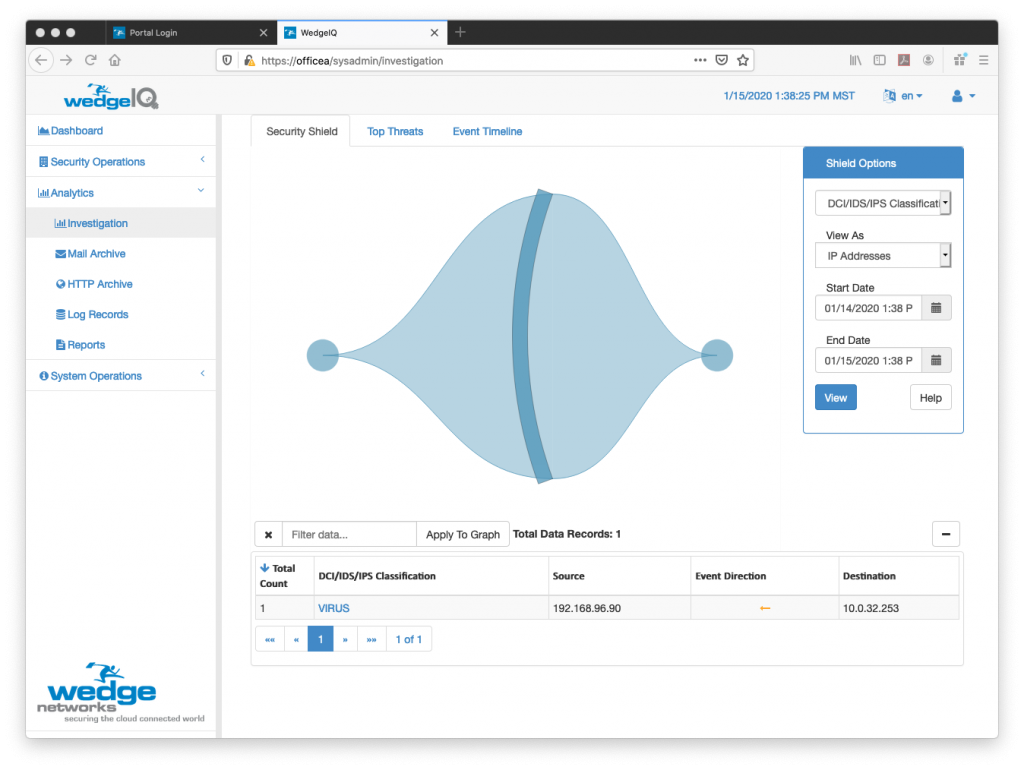
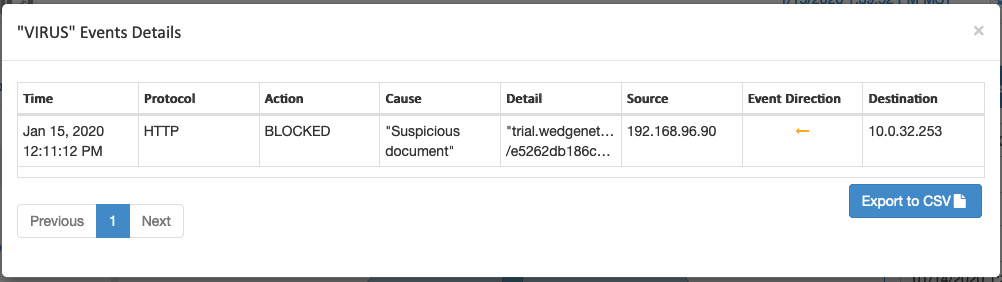
As we covered Healthcare a fair bit last week, I just wanted to pass along some of the recent numbers that reflect the dire situation that the industry continues to find itself in. Forbes published and article a couple of days ago that provides some telling numbers from the US Healthcare industry and a bit of history surrounding how it has been targeted since the first ransomware attack in 1989. Unfortunately, ransomware continues to be the thorn in the side of healthcare even today.
So, down to the numbers. According to a recent report from Comparitech, in the US Healthcare industry alone, 172 ransomware incidents have cost more than $157MM over the past four years. The interesting thing to note is that the actual ransom demands only accounts for 11% of that figure. The OTHER 89% of costs can be attributed to remediation costs and downtime!!
Damage has been incurred across the US, with attacks reported in ALL but five states: Maine, Montana, New Mexico, North Dakota and Vermont. Interestingly, California has been hit the hardest during this time with 25 ransomware incidents reported. Of the more than 1,400 clinics, hospitals and organizations impacted, 75% of attacks have been focused mainly on hospitals and clinics; the front lines of healthcare where downtime can cause life or death situations.
The unfortunate thing is that, although ransomware attacks result in network downtime, reduced patient care and lost time and resources, it is now also frequently targeting the databases that contain highly sensitive and confidential patient records. This is a disturbing trend as, according to the Forbes article, medical records are a hot commodity on the Dark Web marketplaces, where they can often command more than 4 times the price of stolen social security numbers. Factoring in the potential for identity theft, this could potentially cause the total related costs of these ransomware attacks on the healthcare industry to explode!
So, getting back to what the Healthcare Industry can do to help reduce the ongoing effects of ransomware, we refer back to our previous blog. Healthcare has to take a long hard look at what its doing to protect itself. Considering the fact that it’s now 31 years later and the attacks and severity continue to increase, it’s time for the industry to try something new. Instead of the Detect and Remediate approach that has long been in use, and that can be attributed to 89% of the costs that have been incurred over the past 5 years, the industry really has to look at the Detect and Block approach; utilizing a solution that can literally STOP the ransomware from even entering the network. Find out more by contacting our team at: info@wedgenetworks.com and see how you can take advantage of the FREE 90 day trial of the Wedge Advanced Malware Blocker (WedgeAMB) which is spearheading some of the needed security changes in cybersecurity for the healthcare industry.
Main Website Links
Wedge DCI Search
Wedge Calendar
December 2025 S M T W T F S 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 -
Recent Posts
- Wedge Networks Announces General Availability of its Innovative, Continuous Learning Analytics and Threat Intelligence Engine, WedgeIQ™ Nucleation Edition at Asia Tech Singapore
- Wedge Networks Teams up with Edgecore Networks to Offer Next-Generation Network Security WedgeCND™ Add-on Now Available on Edgecore ecCLOUD
- Wedge Networks to Participate at Mobile World Congress 2023
- Wedge Networks to Showcase Latest Innovation In Real-time Threat Prevention, WedgeIQ™ Nucleation Release, at WEST Conference in San Diego February 14-16th
- Wedge Networks Partners with Seaspring to Deliver Real-time Threat Prevention to the Bahrain & MENA Markets
Recent Comments
- Ram Bathala on Calgary’s Wedge Networks Looks to Channel for Enterprise Push with Malware-Blocking Product
- Eva on Milliseconds Versus Minutes – The Difference Between Prevention and Remediation
- Smithb on Wedge Adds AI for Better Malware Blocking
- Abram on Wedge Joins MEF to Boost World’s Third Network Security
- David Millar on 5G & IoT Dominate MWC16
Archives
- June 2023
- May 2023
- February 2023
- January 2023
- November 2022
- September 2022
- August 2022
- July 2022
- June 2022
- March 2022
- February 2022
- January 2022
- December 2021
- November 2021
- September 2021
- June 2021
- May 2021
- April 2021
- March 2021
- February 2021
- January 2021
- December 2020
- November 2020
- October 2020
- September 2020
- August 2020
- July 2020
- June 2020
- May 2020
- April 2020
- March 2020
- February 2020
- January 2020
- October 2019
- August 2019
- July 2019
- June 2019
- May 2019
- April 2019
- March 2019
- February 2019
- January 2019
- October 2018
- September 2018
- August 2018
- July 2018
- June 2018
- March 2018
- February 2018
- July 2017
- June 2017
- May 2017
- April 2017
- February 2017
- November 2016
- October 2016
- September 2016
- May 2016
- April 2016
- March 2016
- February 2016
- December 2015
- November 2015
- October 2015
- September 2015
- August 2015
- June 2015
- May 2015
- April 2015
- March 2015
- December 2014
- November 2014
- October 2014
- April 2014
- March 2014
- February 2014
- January 2014
- December 2013
- November 2013
- October 2013
- April 2013
- November 2012
- October 2012
- September 2012
- June 2012
- May 2012
- April 2012
- March 2012
- February 2012
- January 2012
- December 2011
- November 2011
- June 2011
- May 2011
- February 2011
- November 2010
- October 2010
- September 2010
- August 2010
- July 2010
- June 2010
Categories
Meta
 Kaspersky ThreatPost
Kaspersky ThreatPost- Student Loan Breach Exposes 2.5M Records August 31, 2022
- Watering Hole Attacks Push ScanBox Keylogger August 30, 2022
- Tentacles of ‘0ktapus’ Threat Group Victimize 130 Firms August 29, 2022
- Ransomware Attacks are on the Rise August 26, 2022
- Cybercriminals Are Selling Access to Chinese Surveillance Cameras August 25, 2022
- Twitter Whistleblower Complaint: The TL;DR Version August 24, 2022
- Firewall Bug Under Active Attack Triggers CISA Warning August 23, 2022
- Fake Reservation Links Prey on Weary Travelers August 22, 2022
- iPhone Users Urged to Update to Patch 2 Zero-Days August 19, 2022
- Google Patches Chrome’s Fifth Zero-Day of the Year August 18, 2022